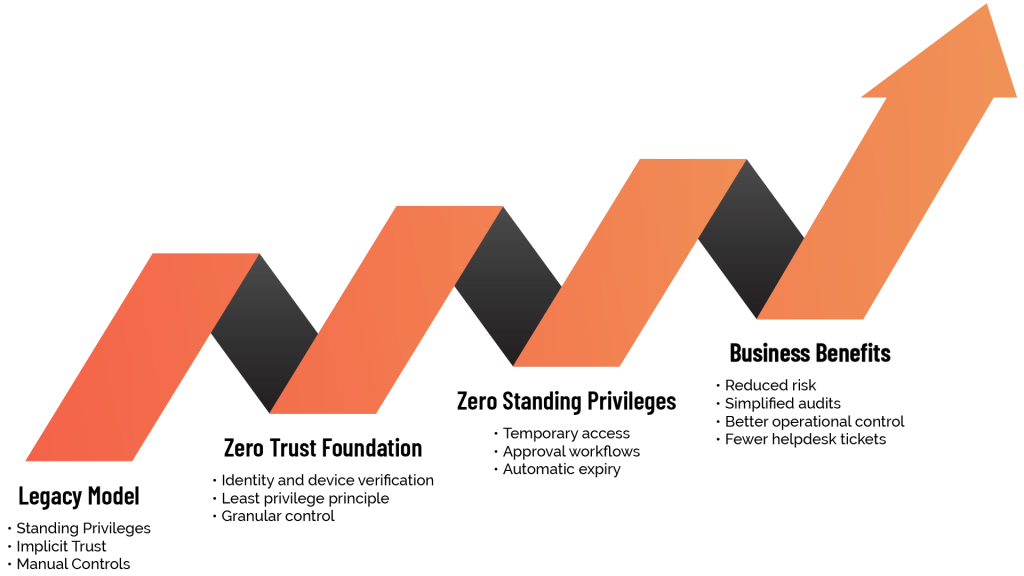
Achieve Zero Trust with Zero Standing Privileges
Eliminate permanent admin rights and embrace just-in-time privileged access with Admin By Request
The cost of standing privileges
of data breaches involve compromised privileged credentials
CyberArk Global Advanced Threat Landscape Report 2023
average savings after a breach for organizations with mature zero trust vs. those without
IBM COST of Data Breach Report 2023
reduction in privileged access incidents with PAM implementation
Delinea State of Privileged Access Report 2023
fewer privilege escalation incidents for organizations using Just-In-Time access
Microsoft Azure Security Benchmark Report 2023
Why Traditional Security Fails
Today’s threat landscape has outpaced outdated strategies like “trust but verify.” Modern enterprises face critical risks:
Persistent access creates long-term vulnerabilities
Overuse of admin rights opens the door to internal breaches
Legacy tools can't keep up with hybrid and cloud-first environments
Limited visibility means blind sports in user behavior and access
Multiple Layers of Zero Trust Security
At the application level, users and endpoints are protected with multiple security features.

Request and Approval Layer
Access requests must be approved by a designated administrator. Role-based access controls and MFA help enforce compliance with frameworks like HIPAA, ISO 27001, and NIST by ensuring only authorized personnel gain elevated privileges.
Threat Detection Layer
All elevated actions are monitored in real time. Files and commands are scanned using 37+ anti-malware engines through OPSWAT Metadefender, supporting data protection and breach prevention requirements.
Logging and Auditability Layer
Every session is logged, including who request access, what actions were taken, and who approved them. Real-time alerts notify security teams of suspicious activity, helping meet audit and documentation obligations.
Tailored Protection to Suit Your Organization
Every organization is different. Admin By Request offers customizable policies that support both security-focused and productivity-focused workflows.
Whatever you choose, you maintain full visibility and control while staying secure and productive.

Security First
For compliance-heavy environments, sensitive data, or large, diverse workforces:
- Mandatory approval for all elevated access
- Credential or MFA authentication
- Realtime alerts for installs or policy violations
- Pre-approval lists restricted to trusted apps
- AI/ML auto-approval disabled
Productivity First
For tech-savvy teams, senior personnel, or phased rollout environments:
- Auto-approval enabled for trusted apps
- Reason prompt optional or bypassed
- Alerting limited to high-risk actions
- Flexible pre-approval workflows
- Minimal user interruption
Whether you’re locked down or scaling back restrictions, Admin By Request puts you in control.
Seamless Integration. Minimal Disruption.
No infrastructure overhaul required. Rapid rollout, immediate protection.

Windows and macOS endpoints
Hybrid and cloud-first environments
Azure AD, OKTA and other IAM solutions
Ready to Tighten Your Security?
Let us show you how easy we can make it to lockdown endpoints, speed up productivity, and stay complaint. Get in touch for a free, 30-minute demo or quote.
FAQs
What is a Zero Trust security model?
A Zero Trust security model assumes that no user, device, or application should be trusted by default, even inside the network. Instead, all access must be continuously verified. Admin By Request supports Zero Trust by enforcing least privilege, real-time access validation, and continuous monitoring of privileged activity.
What is Just-in-Time (JIT) access?
Just-in-Time access is a key Zero Trust principle that provides users with temporary elevated privileges only when they need them, and revokes access automatically after use. Admin By Request enables JIT access by allowing users to request elevation, enforcing approval workflows, and logging all elevated activity.
How does Just-in-Time access improve security?
JIT access dramatically reduces the risk of credential theft, privilege misuse, and lateral movement. By removing always-on admin rights, Admin By Request limits the attack surface and shortens the window of opportunity for insider and external threats alike.
How does Admin By Request help implement Zero Trust?
Admin By Request enforces Zero Trust by:
- Eliminating standing privileges
- Verifying identity and device at each request
- Requiring access justification and approval
- Logging all privileged sessions for review
- Integrating with SSO, MFA, and endpoint policies
It provides practical, real-world Zero Trust enforcement with minimal disruption to users.
Can Just-in-Time access work across remote or hybrid environments?
Yes, Admin By Request is built to support remote, hybrid, and cloud-first workforces. It integrates with Windows, macOS, and cloud-based identity providers to deliver consistent JIT enforcement across all endpoints.
Does Just-in-Time access impact user productivity?
Not with Admin By Request. The platform enables fast, secure access with minimal friction. Users can request elevation, receive approval, and complete tasks quickly. Pre-approved applications, AI auto-approval, and customizable workflows keep teams productive while security stays tights.