Endpoint Privilege Management
An award winning, comprehensive, and secure SaaS-based solution to standing admin rights that's lightweight, easy to deploy, and simple to use
Why Choose Admin By Request?
No password vault to breach, a sub-3MB agent, no training required, and less than 1% CPU utilization. Our ultra-lightweight privilege management will secure your endpoints fast, with no infrastructure overhaul.
Secure Application or user elevation
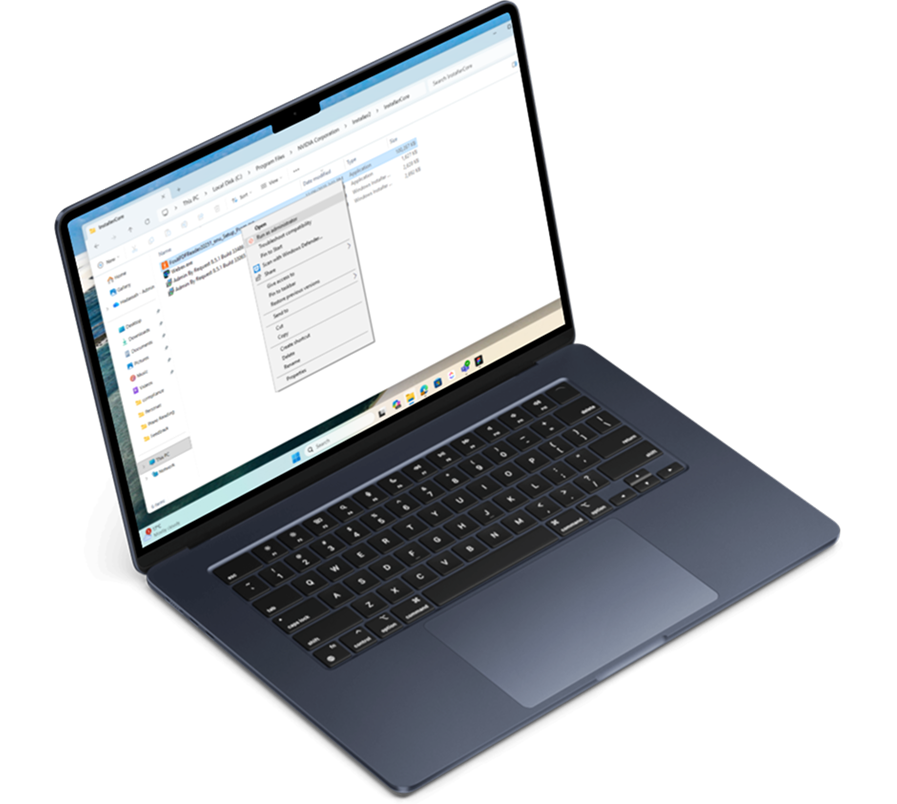
with session timer
Full audit logging

and reason tracking
Approve or deny requests

in seconds
MFA/SSO endpoint enforcement

and IDP integration
Complexity is Your Biggest Vulnerability

Your Users Already Know How To Use Our Software
The strongest security solution is the one that actually gets used.
With Endpoint Privilege Management’s invisible simplicity, users continue their normal workflow without learning new processes or waiting for approval. When they need to install new software or change settings, it just works.
You Don't Have to Choose
End the struggle between giving users admin rights or drowning your helpdesk in install requests. Just deploy our endpoint software and free up your IT resources.
Our client automatically intercepts installations, scans with 37+ antivirus engines, and executes with full admin privileges while keeping users as standard accounts. Approve every request or use AI and machine learning to speed up the process, with granular security and privacy settings for your unique risk tolerance.
Our OFFLINE agent installers are less than 3MB, and average use requires under 1% endpoint CPU utilization.
Granular access and app control
Key Features You'll Love
With no hidden costs and no paid add-ons, modules, or extensions
Boost Productivity
Run as Admin
Admin Session
PIN code
Pre-approval
Application blocking
Simplify Compliance
Full audit logging
Session recording
MFA/SSO endpoint enforcement
Reason Tracking
Granular privacy
Lock Down Security
Break glass/LAPS
Device owner
Just-in-time elevation
Malware scanning (37+ engines)
Tamper prevention
Automate & Streamline
AI auto-approval
Machine learning
IdP Integration
Clean Up Local Admins
Mobile App
Handcrafted in Denmark By System Administrators for System Administrators





Smooth Integration. Minimal Disruption
Admin By Request works seamlessly across remote environments with no heavy infrastructure changes:

Windows, macOS and Linux endpoints
Hybrid, remote, and cloud-first environments
Integrations with VPNs, RMM tools, IAM platforms (Azure AD, Okta).
Let us show you.
At your fingertips
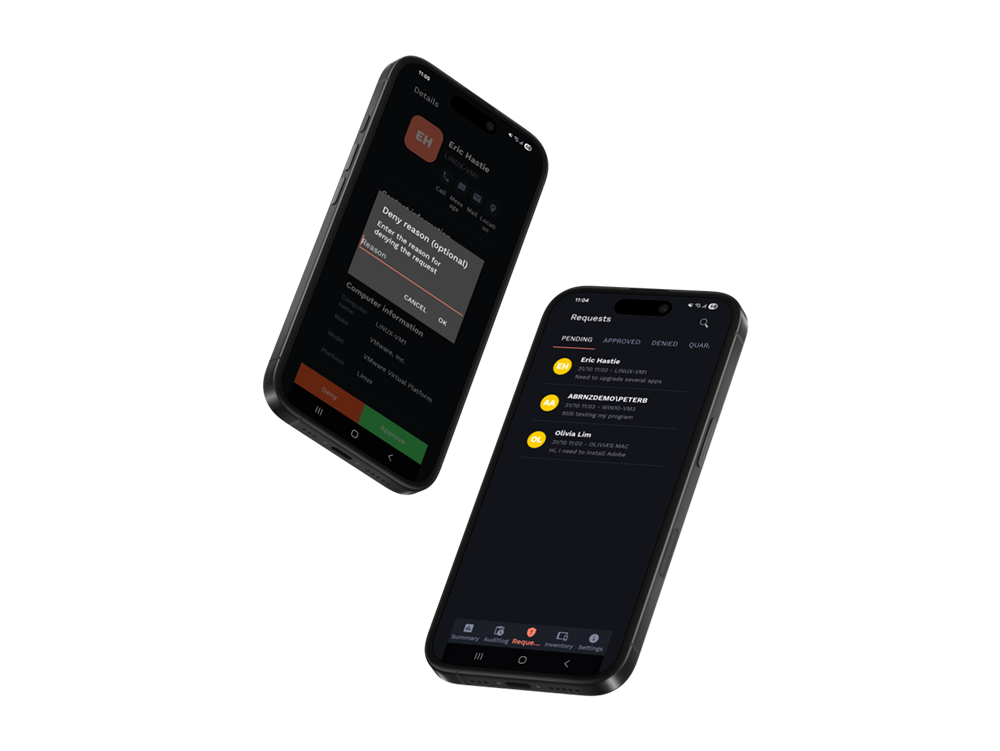
The Mobile App
The mobile app makes approving requests easy for your team. A request for privileges will be pushed, real-time, to your administrators’ phones.
The more app gives you access to your full audit log and inventory from your pocket without you having to go to the web portal for data.
All Features, 25 Seats, Completely Free
Your free plan includes 25 licenses for our Endpoint Privilege Management and Secure Remote Access products, so you can see just how easy it is to lock down endpoints, manage security, and support your workforce wherever they are.
FAQs
What is Endpoint Privilege Management and how does it improve endpoint security?
Endpoint Privilege Management (EPM) is a form of Privileged Access Management (PAM) that controls administrative privileges across endpoints. Rather than requiring permanent admin rights, EPM provides just-in-time privilege elevation with audit trails. This eliminates the common dilemma of choosing between giving users full admin access or forcing them to submit tickets for every software installation. EPM significantly improves endpoint security because when malware compromises an endpoint, it can only operate with standard user privileges instead of full administrative control.
How does Admin By Request's EPM solution work without requiring permanent admin rights?
Admin By Request EPM intercepts privilege requests at the system level and elevates only the specific application or process that needs admin rights, not the entire user session (when using Run as Admin – single app elevation). This sandboxed approach allows users to install software autonomously while maintaining policy enforcement. You get two elevation modes: Run As Admin for individual applications and Admin Session for time-limited full administrative access.
What makes Admin By Request different from traditional allowlist solutions?
Our EPM product includes allowlist capabilities through Pre-Approval, where administrators can create policies based on file location, vendor certificates, or checksums. What sets us apart from other enterprise cybersecurity solutions is flexibility in how these allowlists are built and maintained. Machine learning automatically adds frequently approved applications to allowlists, AI approval uses application popularity scores, and you can quickly pre-approve applications directly from audit logs. You can start with traditional allowlist approaches but evolve to more dynamic, data-driven policies.
Can the EPM solution work for both online and offline endpoints?
Yes, Admin By Request EPM works whether endpoints are online or offline. Portal settings and elevation logs are cached locally on each device and sync when connectivity is restored. For offline scenarios requiring manual approval, administrators can generate unique PIN codes that users enter to complete their elevation requests. This ensures business continuity even when devices can’t reach the corporate network.
What happens if a user gets disconnected from the domain or needs emergency admin access?
Admin By Request EPM includes a Break Glass feature that generates a one-time, time-limited full local admin account on any endpoint with a single click. This enhanced LAPS solution is ideal for emergency situations where a user becomes disconnected from the directory and no permanent admin account exists on the device. Break Glass accounts are fully logged in the portal, and all processes elevated under these accounts are audit logged for complete visibility.
How does the solution help with compliance and auditing requirements?
Endpoint Privilege Management includes audit and asset tracking features as standard. Every privilege elevation is logged with detailed information including user identity, application details, timestamps, and approval decisions. The system provides filterable views of all managed computers, reporting of installed software and hardware, and API access for integration with SIEM tools. All elevation activity can be exported in PDF, XLS, or CSV formats for compliance reporting.
Does Admin By Request require minimum service hours or additional infrastructure?
No, we don’t require customers to purchase minimum service hours. Our Zero Trust platform is built for ease of use, allowing most organizations to deploy and manage it without ongoing support costs. There’s also no on-premises infrastructure required (no servers, VM appliances, or databases). It’s a SaaS-based solution that you can start testing immediately with our Free Plan covering up to 25 endpoints.
Do you provide setup and configuration services?
Admin By Request EPM is designed to be intuitive enough that most organizations can deploy it without professional setup services, even across thousands of endpoints. However, if you prefer assistance with configuration or other aspects, our team is happy to offer that support.
What operating systems and deployment methods does the EPM solution support?
EPM supports Windows, macOS, and Linux endpoints with cross-platform licensing. The lightweight agent (under 2MB) deploys using standard tools like SCCM, Microsoft Intune, or Jamf. It works across diverse environments including standalone workgroups, multi-domain Active Directory, and Entra ID deployments. The same EPM policies and audit capabilities apply consistently across all supported platforms.
How quickly can organizations see results after implementing Endpoint Privilege Management?
Organizations typically see immediate endpoint security improvements once admin rights are revoked and Admin By Request EPM is deployed. The pre-revocation logging feature allows you to understand current admin usage patterns before making changes. Most customers report reduced helpdesk tickets within weeks of deploying our PAM product.





