Every IT team faces the same vendor access dilemma: you need to give third-party contractors secure access to specific internal systems, but traditional approaches force you to choose between security and convenience. VPNs create persistent tunnels that expand your attack surface. Jump servers require complex infrastructure. As for directly exposing systems to the internet, that’s a security nightmare waiting to happen.
There’s a better way. By combining Cloudflare’s global edge network with Admin By Request’s Secure Remote Access solution, organizations can provide vendor access that’s both highly secure and surprisingly simple to deploy.
The Vendor Access Problem
When you give a contractor VPN access, that connection stays active for the entire duration of their project. They can connect during off-hours when your team isn’t actively monitoring network activity. The tunnel exists whether they’re actively working or not, creating a persistent pathway into your network that you can’t easily control.
Jump servers and bastion hosts seem more secure on the surface, but they create single points of failure and require dedicated infrastructure that needs patching, monitoring, and maintenance. You’re essentially running additional servers just to provide temporary access to external parties.
Even worse, these traditional approaches operate on an implicit trust model. Once authenticated, vendors typically have broad access within their designated network segments. There’s no granular, real-time control over what they can actually reach or do during their sessions.
How Cloudflare Tunnels Work
Cloudflare tunnels solve the vendor access problem by flipping the traditional network security model. Instead of punching holes in your firewall, your endpoints create secure outbound connections to Cloudflare’s global network.
Your internal systems never accept inbound connections. When a vendor needs access, your endpoint establishes a secure tunnel through Cloudflare’s infrastructure that vendors can access through their web browsers while your firewall rules remain locked down.
Whether vendors are connecting from across town or across the globe, they’re routed through the nearest Cloudflare edge location for optimal performance.
Admin By Request’s Zero Trust Implementation
Admin By Request’s Secure Remote Access solution takes Cloudflare’s tunneling technology and wraps it in a complete zero trust framework. Instead of giving vendors broad network access, the system provides just-in-time, scoped access to specific systems.
The process works like this: vendors navigate to a dedicated portal at access.work (separate from your main Admin By Request portal) and authenticate using single sign-on, which must be configured as a prerequisite. The system checks their permissions, which you’ve pre-configured to limit exactly which systems they can reach, and if approved, establishes a secure WebSocket connection through the Cloudflare tunnel.
The vendor gets a browser-based interface that lets them control the remote system using RDP, SSH, or VNC protocols, depending on what they need. Meanwhile, every action is logged, recorded, and auditable. When the session ends, the tunnel is torn down completely.
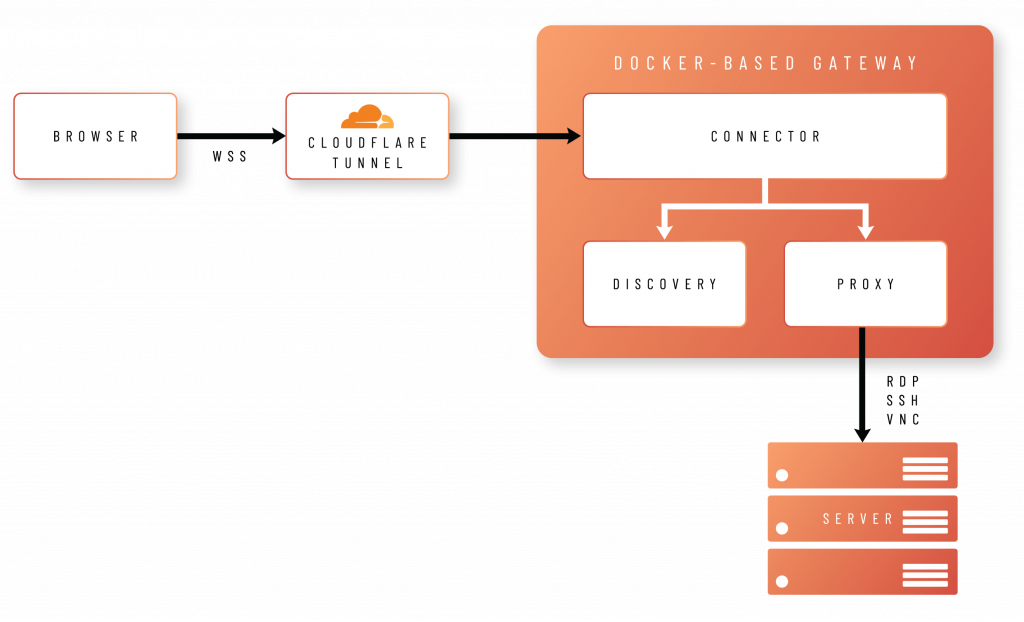
What makes this particularly powerful is the three-container architecture running behind the scenes:
- Connector handles authentication and communication with Admin By Request’s portal
- Proxy manages the actual protocol connections (RDP, SSH, VNC)
- Discovery can automatically find systems on your network that need to be accessible, without requiring agents on every machine
Real-World Implementation Benefits
The security advantages are immediately apparent. Your vendors never get direct network access, and there are no standing permissions or persistent connections. Every session requires explicit approval and has configurable time limits. You can enable view-only access for certain vendors, require multi-factor authentication, or set up automated session recordings for compliance.
The operational benefits are equally impressive. Deployment takes minutes, not weeks. For cloud-hosted gateways, you simply configure your endpoints and set up vendor permissions in the Admin By Request portal. If you prefer self-hosted infrastructure, the entire gateway stack deploys via Docker Compose.
Vendors appreciate the streamlined experience: no VPN software to install, no complex connection procedures, and no waiting for IT to provision access. They authenticate once and get immediate, browser-based access to exactly what they need.
The Technical Architecture That Makes It Possible
This works through a carefully orchestrated sequence. When a vendor initiates a connection, Admin By Request’s client on your target endpoint receives an instruction via MQTT broker to fetch settings. Those settings instruct the client to open a Cloudflare tunnel using an outbound UDP call on port 7844 with the QUIC protocol.
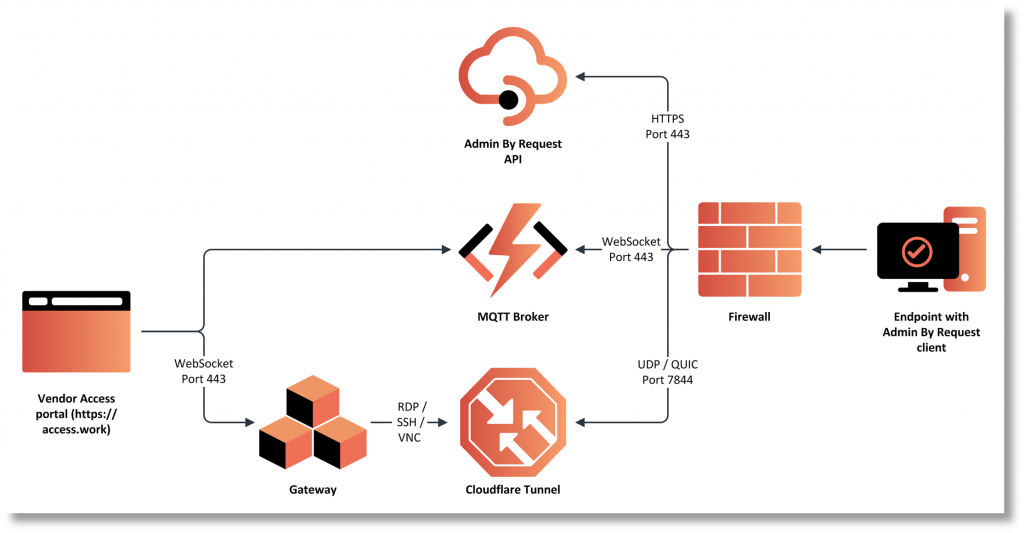
Simultaneously, the gateway infrastructure (whether cloud-hosted or on your premises) receives instructions to forward the appropriate protocol connection through that tunnel. A secure WebSocket connection bridges the vendor’s browser to your internal system, with all traffic flowing through Cloudflare’s encrypted infrastructure.
This architecture eliminates inbound firewall rules while providing enterprise-grade security and the reliability that makes remote access actually usable.
Scaling and Deployment Flexibility
Unlike traditional remote access solutions that become unwieldy as you add more vendors and systems, this approach actually scales gracefully. Need to give a new contractor access to different systems? Just configure their scope in the portal. Working with vendors across multiple time zones? The global Cloudflare network ensures consistent performance everywhere.
For larger organizations, the system supports multiple gateway deployments, letting you distribute access by department, geography, or security requirements. You can even mix cloud-hosted and self-hosted gateways within the same deployment, giving you maximum flexibility.
The discovery capabilities become particularly valuable at scale. Instead of manually cataloguing every system that might need vendor access, the discovery container can scan your network segments and automatically identify accessible systems. This means your vendor access capabilities grow automatically as your infrastructure evolves.
Enterprise-Grade Controls and Auditability
What sets this approach apart from simple screen-sharing tools is the enterprise-grade controls and auditability. Every vendor session generates detailed logs showing exactly what was accessed, when, and by whom. Optional session recording creates video evidence of all activities, which proves invaluable for compliance audits or security investigations.
The approval workflows provide granular control over vendor access. Vendors may see different icons when requesting access: a key icon means credentials are required, a locked icon indicates manual approval is needed, while an unlocked icon shows pre-approved access. This visual system makes the approval state immediately clear to both vendors and administrators.
You can configure user scoping to limit vendors to specific computer types, domains, organizational units, or network gateways. This ensures vendors only see and can access systems relevant to their work, with no visibility into broader network resources.
The approval workflows can be customized to match your organization’s requirements:
- Pre-approved access for trusted vendors to specific, low-risk systems
- Manual approval workflows requiring IT sign-off for each session
- Automated session timeouts that force re-authentication after set periods
- Multi-factor authentication requirements for accessing sensitive systems
- Custom approval chains with different requirements based on access type
Integration with existing identity providers means vendors use familiar authentication methods, while the API enables integration with ticketing systems, SIEM platforms, or other security tools your organization already uses.
Vendor Access as Zero Trust Foundation
The vendor access challenge highlights how traditional perimeter-based approaches work well for internal users, but break down when you need to regularly grant access to external parties. The result is often a choice between security and operational efficiency.
This Cloudflare-powered approach demonstrates zero trust principles in action: authenticate every connection, authorize specific access, and monitor all activity regardless of network location. Vendors don’t get “inside” your network – they get precisely the access they need with full visibility into their activities.
For organizations looking to implement zero trust architectures, secure vendor access often serves as a proving ground for these concepts before applying them more broadly across internal systems and remote employees.
Frequently Asked Questions
Q: Do vendors need to install any software or have special network configurations?
A: No. Vendors access your systems entirely through their web browser using the access.work portal. There’s no VPN client, remote desktop software, or browser plugins required. They just need standard internet access and a modern web browser – no special firewall or network requirements on their end.
Q: What happens if a vendor’s session gets disconnected?
A: The Cloudflare tunnel is automatically terminated when the session ends, whether intentionally or due to network issues. Vendors would need to re-authenticate and get approval for a new session to reconnect.
Q: Can we limit vendors to specific servers or applications, not just network segments?
A: Yes. You can configure user scoping to restrict vendors to specific computer types, domains, organizational units, or individual systems. Vendors only see and can access what you’ve explicitly granted them permission to reach.
Q: How does this work with our existing firewall rules?
A: Your firewall configuration doesn’t need to change. All connections are outbound from your endpoints to Cloudflare’s network using UDP port 7844. No inbound firewall rules or port forwarding required.
Q: What protocols does this support for remote access?
A: The system supports RDP for Windows systems, SSH for Linux/Unix systems, and VNC for cross-platform access. The protocol is selected automatically based on the target system.
Q: Can we record vendor sessions for compliance purposes?
A: Yes. Session recording can be enabled to create video recordings of all vendor activities. These recordings are stored in the audit log and can be downloaded for compliance reviews or security investigations.
Q: How quickly can we revoke a vendor’s access?
A: Vendor access can be revoked immediately through the Admin By Request portal. Since sessions are just-in-time, revoking access prevents new connections but doesn’t affect any active sessions until they naturally expire or are manually terminated.












