Local Admin Rights, Managed.
Lock down endpoints, secure remote employees, and meet compliance goals with no disruptions.







































''We use Admin By Request to manage local admin rights at Atos on more than 100.000 endpoints in 60 countries. We would definitely recommend Admin By Request to any organization looking to solve the local admin rights problem.''
Trusted by Global Leaders
Latest News
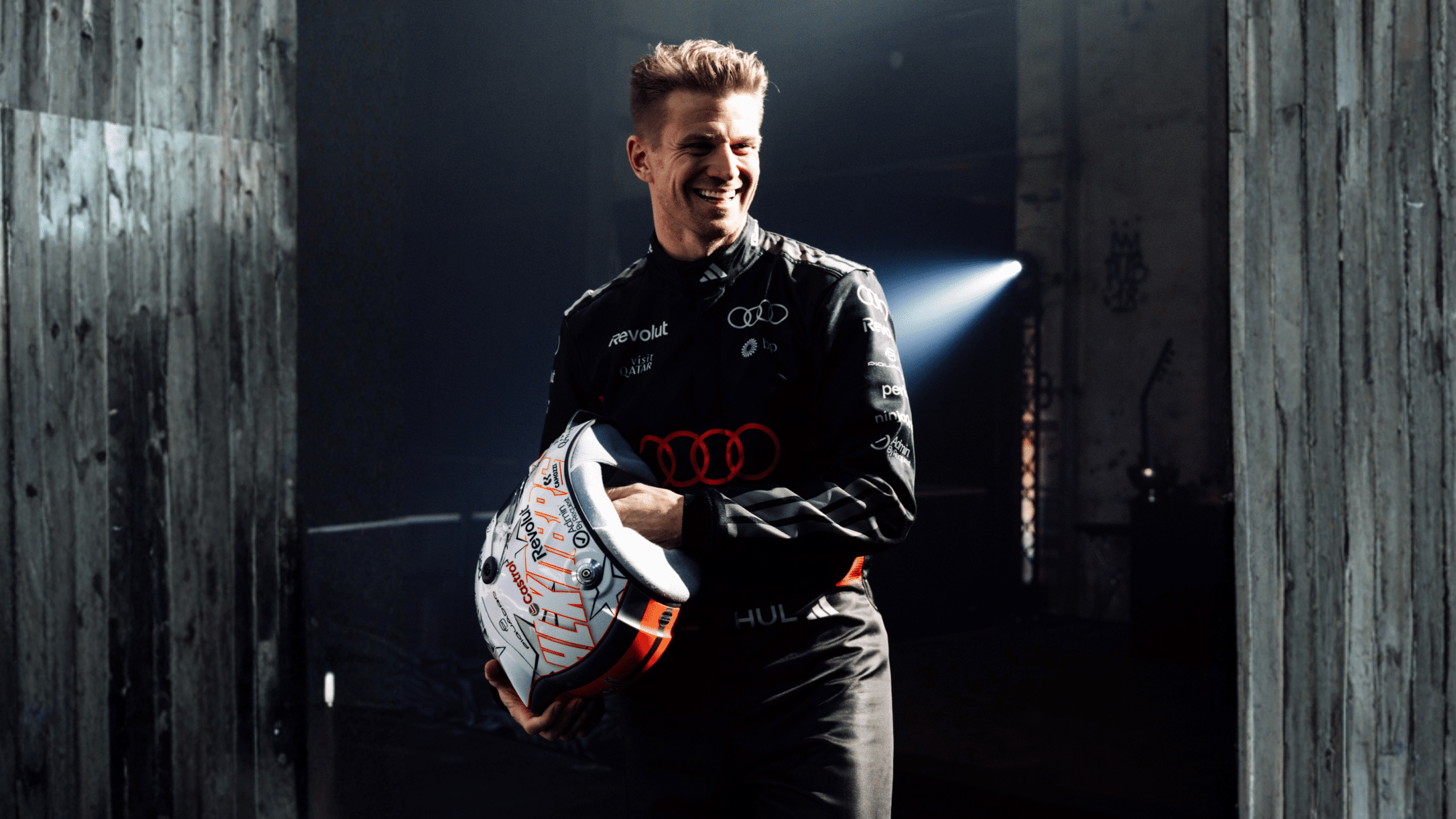
2026 Formula 1 Partnership
Admin By Request is proud to renew partnership with Audi F1® Project driver, Nico Hulkenberg.
Full control at your fingertips.
App Elevation
Elevate applications without elevating the user
Break Glass / LAPS
Provision temporary local admin accounts
Malware Detection
Multi-scanning with over 35 engines
Compliance
Meet regulatory compliance requirements
Endpoint MFA/SSO
Enforce business rules with MFA and SSO prior to elevation
AI Approval
Allow our AI engine to auto-approve requests for elevation
Machine Learning
Allow auto-approvals after a set number of manual approvals
Remote Access
Enabling secure, efficient connectivity to servers.
Multi-Platform
Versions for Windows, macOS, and Linux operating systems
ServiceNow
Remove the need to access the Portal - get core features in ServiceNow
Integrations
Teams, Slack, Splunk, Sentinel, Power BI, Intune, and more
Mobile Application
Access User Portal features from your mobile device
Product Executive Summaries
Improve your Workflow
Integrate
Admin By Request
With your favourite software tools.




Product Explainer Video
Endpoint Privilege Management (EPM)
Bridge the gap between security and user productivity.
People we've helped
Here's what they're saying
Problem | Solution | Implementation
Case Studies
Get Protected
Sign up for our Free Plan
No strings attached.
Our free, lifetime subscription comes with all core features and is available for up to 25 endpoints, on Windows, macOS, and Linux. Fill out the form, sign in to your account, download the lightweight client, and get protected today.
Lightweight client, heavyweight protection
Fill out the form with your work email and we’ll send you your log in credentials.





