VPN Security Vulnerabilities
How secure is your remote access solution? In a world where remote work has become the new normal, ensuring safe access to servers and network infrastructure is more critical than ever. With cyber threats evolving daily, even established technologies like Virtual Private Networks (VPNs) are being pushed to their limits. The Cybersecurity and Infrastructure Security Agency (CISA) has flagged numerous VPN vulnerabilities, issuing emergency directives to safeguard federal systems. The recent Ivanti VPN exploit exposed just how fragile traditional VPNs can be. In this post, we’ll break down the Ivanti incident, explore the flaws of conventional VPNs, and introduce Admin By Request’s Remote Access solution as a more secure alternative.
The Ivanti VPN Exploitation: A Wake-Up Call
The Ivanti incident brought attention to the cybersecurity community, revealing the potential challenges of relying on conventional VPNs for secure remote access. The exploits involved hackers taking advantage of two previously unknown weaknesses (zero-day vulnerabilities) in Ivanti’s Connect Secure and Ivanti Policy Secure products. These vulnerabilities allowed the attackers to bypass security measures, gaining unauthorized access to VPN gateways/appliances.
The first vulnerability (CVE-2023-46805) enabled the attackers to bypass authentication, granting them access to restricted resources without the proper credentials. The second vulnerability (CVE-2024-21887) allowed the attackers to execute specially crafted commands on the Ivanti VPN, essentially taking control of the system.
This incident underscores the broader implications of VPN access vulnerabilities, highlighting the critical need for organizations to address these risks proactively. Alternative solutions, such as Privileged Remote Access, can mitigate these threats and enhance security.
Once inside, the attackers could engage in various malicious activities, including stealing sensitive data and compromising target organizations’ IT systems. The scale of the attack was widespread, affecting thousands of Ivanti VPN appliances globally and impacting organizations across different industries.
Understanding Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) have long been the cornerstone of remote access strategies. They work by creating an encrypted tunnel between the user’s device and the corporate network, ensuring data confidentiality and integrity, but VPN technology also comes with inherent risks such as broad network access and exposure to malicious actors. VPNs are trusted for their simplicity and widespread use, providing a secure conduit for employees to connect to their organization’s internal infrastructure from anywhere in the world.
Security Risks in Traditional VPNs
The recent Ivanti VPN incident exposed the dangers of VPN vulnerabilities, shedding light on the potential security risks and disadvantages associated with these solutions. Traditional VPN technology creates broad network access rather than specific, controlled access, raising security concerns regarding vulnerabilities and trust issues. Below we delve into the various pitfalls and consequences linked to traditional VPN software, which enterprises should carefully consider when formulating their remote access strategy.
Inbound Requests and Vulnerabilities
- Challenge: Traditional VPNs often rely on inbound requests for access, making them susceptible to exploitation. Inbound requests can provide a potential entry point for attackers, especially if vulnerabilities exist in the VPN software.
- Impact: Recent events, such as the Ivanti VPN exploitation, have highlighted the potential dangers of such vulnerabilities – attackers may attempt to exploit weaknesses, conduct unauthorized access, and potentially compromise the network’s security.
VPN Security and Limited Granular Control
- Challenge: Traditional VPNs may offer limited granularity in terms of access controls and user permissions. Admins might face challenges in implementing detailed access policies.
- Impact: This limitation can lead to challenges in ensuring that users have appropriate access levels and that sensitive resources are adequately protected.
Potential for Split Tunneling Risks
- Challenge: Some VPN configurations allow split tunneling, where only traffic destined for the corporate network is sent through the VPN. This introduces potential security risks.
- Impact: If not configured securely, split tunneling can expose users to threats when accessing the internet directly, bypassing the protective measures applied to corporate traffic.
Reliance on Traditional Authentication
- Challenge: Traditional VPNs often rely on username and password authentication, which can be vulnerable to credential-based attacks.
- Impact: If user credentials are compromised, attackers can gain unauthorized access to the VPN, potentially leading to data breaches, lateral movement, and other security incidents.
Limited Support for Zero Trust Models
- Challenge: Traditional VPNs may not seamlessly align with Zero Trust models, which prioritize continuous verification and least privilege access. Achieving a Zero Trust architecture within the existing framework of traditional VPNs often requires additional security measures.
- Impact: The incongruence with Zero Trust models poses a potential security risk, as traditional VPNs might struggle to enforce the stringent access controls and continuous monitoring required for a robust Zero Trust security posture. Organizations may face difficulties in implementing a comprehensive Zero Trust strategy without integrating supplementary security measures.
Understanding these weaknesses highlights the importance of exploring more secure alternatives, such as Admin By Request’s Remote Access solution.ese weaknesses highlights the importance of exploring more secure alternatives, such as Admin By Request’s Remote Access solution.
Admin By Request Remote Access: A Superior Alternative
Admin By Request Privileged Access Management (PAM) now offers Remote Access: a feature that redefines the way organizations approach secure remote connections, providing a robust alternative to traditional VPNs. Traditional VPN solutions have significant limitations and vulnerabilities, necessitating the adoption of more secure alternatives like zero trust architecture.
How It Works: The core concept of the solution is to empower users to connect to remote servers effortlessly through their browsers. This is achieved by establishing a Secure WebSocket connection to a gateway, facilitated through a secure Cloudflare tunnel.
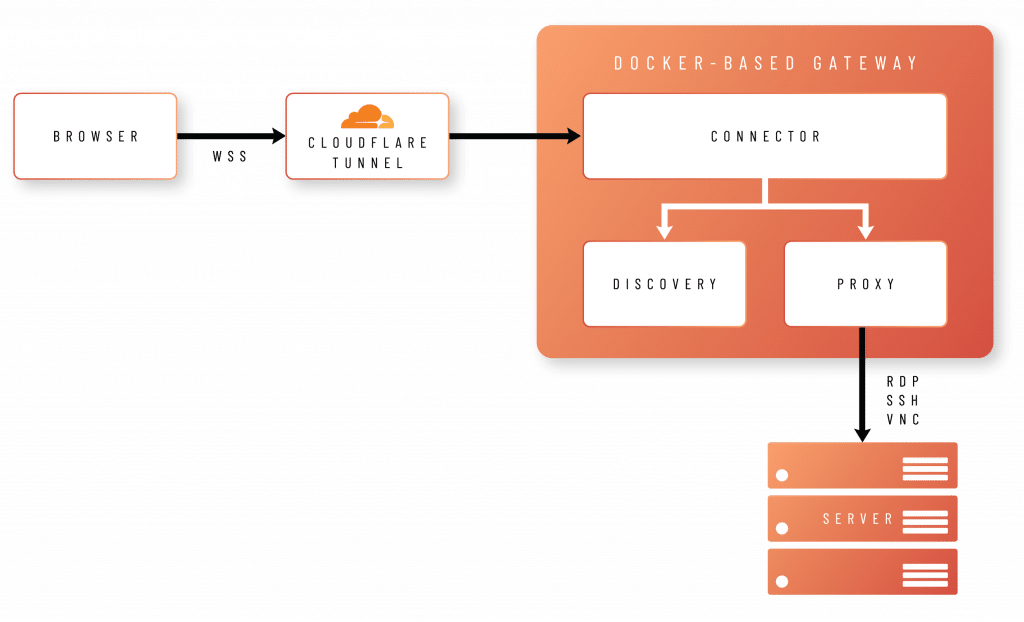
The service can be hosted on-premises or as a fully managed cloud service:
- Cloud-Managed Setup: In a cloud-managed setup, the customer’s server establishes an outbound connection or tunnel to the gateway within Admin By Request infrastructure. Users can then connect directly to the gateway, which maintains a direct connection to the desired server.
- On-Premises Setup: Similar principles apply to the on-premises setup where the gateway is hosted within the customer’s infrastructure: the server initiates a connection with the gateway within the customer’s infrastructure. Using a Cloudflare tunnel, this gateway enables direct external connections.
Secure Outbound Requests
The connection method described above presents a lower security risk compared to the typical inbound requests associated with VPNs. Inbound requests in traditional VPNs carry a higher risk of unauthorized access from external entities, serving as potential entry points for attackers – like the scenario witnessed in the Ivanti exploit. Additionally, in both cloud-managed and on-premises configurations, connections are initiated either by the gateway or endpoint, eliminating the need for network changes (such as adjusting firewall rules) within the customer’s infrastructure. By ensuring that all user traffic is routed through a secure gateway, Admin By Request also removes the threats associated with VPN split tunneling.
Support for External Access
With Admin By Request’s setup, there’s no need to incorporate external users into your Active Directory or VPN solution. Instead, you can maintain a secure workflow by implementing the tried and tested Admin By Request approval process. Users seeking access to the server must go through an approval system, ensuring controlled and time-limited connections without the necessity of integrating external users into your internal infrastructure.
Access Controls & Monitoring
Admin By Request’s Remote Access utilizes extensive Privileged Access Management (PAM) capabilities, allowing enterprises to define granular access rules for users and groups via a simple web interface. These access controls ensure all users have the appropriate access to critical infrastructure around the clock, minimizing headaches for IT. User permissions are monitored via the Admin By Request Admin Portal, triggering alerts in case of lateral movement – another tactic used in the Ivanti VPN attacks. These features align with a Zero Trust model: enforcing least privilege principles and continuously monitoring user activity.
Comprehensive Visibility
Traditional VPNs often fall short when it comes to providing visibility on user activity during remote sessions. Access to servers instigated via Admin By Request is fully audited and video recorded, enabling enterprises to track exactly what’s gone on during a remote session.
Diverse Authentication Methods
Admin By Request Remote Access offers authentication via Just-In-Time (JIT) accounts, which terminate after use, as well as support for native credentials (username and password). This flexibility in authentication options when connecting to servers helps to reduce the risk of credential-based attacks and ensures a robust approach to safeguarding access. Organizations are increasingly adopting zero trust network access (ZTNA) as a more secure alternative to traditional VPNs, highlighting a shift in workforce connectivity strategies to enhance overall security posture.
Conclusion: Embracing a New Era of Remote Access Security
The Ivanti VPN exploitation serves as a stark reminder that the traditional approach to remote access is not infallible. Admin By Request’s Remote Access product emerges as a game-changer, offering organizations a secure, user-friendly, and innovative alternative to traditional VPNs.
Try it today as part of Admin By Request Server Edition, available on a lifetime Free Plan at the link below.
Sources:
- Svenska företag hackade via säkerhetshål i Ivanti vpn – Computer Sweden (idg.se)
- State-Sponsored Hackers Exploit Zero-Day Flaws in Ivanti VPN (pcmag.com)
- www.itpro.com
- Hackers begin mass-exploiting Ivanti VPN zero-day flaws | TechCrunch
- Threat Actors Exploiting Ivanti EPMM Vulnerabilities | CISA
- Active Exploitation of Two Zero-Day Vulnerabilities in Ivanti Connect Secure VPN | Volexity











