Remote Desktop (RDP) allows you to access and control a remote computer from another device, perfect for remote work, troubleshooting and managing servers. This guide to Remote Desktop will walk you through the setup so you can connect easily.
What is Remote Desktop and Why Use It?
Remote Desktop enables users to work remotely by accessing a PC’s files, applications, and network resources from another location. It’s a great tool for IT support, remote work scenarios, and accessing company resources from afar.
Enabling Remote Desktop on Your PC
- Steps to Enable RDP:
- Navigate to Settings > System > Remote Desktop.
- Ensure your PC runs Windows 10 Pro or Enterprise, or Windows 11 Pro or Enterprise.
- Enable Remote Desktop on the desired PC and verify it is connected to the same network as the remote device.
- Requirements:
- Make sure your device meets the necessary requirements, and the Remote Desktop feature is enabled in the system settings.
Setting Up a Remote Desktop Connection
- Using the Microsoft Remote Desktop App:
- Download and open the Microsoft Remote Desktop app.
- Enter the name or IP address of the remote PC in the ‘Computer’ field and select ‘Connect’.
- Enter your credentials and select ‘Remember Me’ to save your details for future sessions.
- Connecting from Various Devices:
- The Remote Desktop app supports connections from Mac, iOS, and Android devices, providing flexibility for accessing your PC remotely.
Configuring Your Network for Remote Desktop
- Firewall and Network Settings:
- Configure your firewall to allow remote desktop connections.
- Ensure that the appropriate ports are open, and consider setting up Network Level Authentication (NLA) for an additional security layer.
- Port Forwarding:
- Set up port forwarding on your router to enable connections from outside your local network, if necessary.
Troubleshooting Common Issues
- Firewall Configuration:
- Verify that your firewall is not blocking RDP connections.
- Network and Device Checks:
- Ensure the remote PC is on and connected to the same network as your device. If issues persist, use the computer’s IP address instead of its name to connect.
Security Considerations for Remote Access
Remote Desktop is a powerful tool, but security in remote desktop is crucial for several reasons:
Protection Against Unauthorized Access
Remote access allows users to connect to a system or network from anywhere which can be exploited by malicious actors. Without proper security in place, unauthorized users could access sensitive systems and data, resulting in data breaches, unauthorized changes or even complete control of critical systems.
Protecting Sensitive Data
Many remote access sessions involve sensitive data such as personal information, financial records or intellectual property. Security measures like encryption, multi-factor authentication and secure protocols ensure this data is protected during transmission and access, so it can’t be leaked or accessed unauthorized.
Preventing Malware and Ransomware Attacks
Remote access can be a vector for malware and ransomware attacks if credentials are compromised or security is weak. Strong security measures verify the user, secure the communication channel and monitor for suspicious activity to reduce the risk of attacks.
Meeting Compliance Requirements
Many industries are subject to strict data protection regulations that require secure remote access. Regulations like GDPR, HIPAA and PCI-DSS have specific security requirements for data. Having proper security in place ensures compliance with these regulations and avoids legal and reputational risk.
Maintaining Business Continuity
Security breaches can cause significant downtime and disrupt business. By securing remote access businesses can continue to operate even when employees need to work remotely or access systems offsite. This is especially important in crisis situations like natural disasters or pandemics.
Keeping Customer Trust and Reputation
Customers expect their data to be secure. A breach caused by poor remote access security can damage a company’s reputation and erode customer trust. Having proper security in place protects the company’s brand and builds trust with customers and partners.
It’s not just about data, it’s about the entire organization and its stakeholders.
Reducing risk when using Remote Desktop
- Best Practices:
- Only enable Remote Desktop on trusted networks, such as your home or corporate network.
- Ensure all user accounts with access have strong, unique passwords.
- Advanced Security Measures:
- Use Network Level Authentication (NLA) to require users to authenticate themselves before accessing the remote system. This adds an essential layer of security.
A Safer Alternative: Admin By Request Remote Access
Traditional RDP setups are convenient but can be a risk if not properly secured. Admin By Request Secure Remote Access with Server Edition has several benefits because it’s built on the solid foundation of our flagship Privileged Access Management (PAM) product. Here are some of the key features and benefits:
Browser-Based Access
Admin By Request Secure Remote Access allows time limited remote access to internal systems directly from a browser interface, so you don’t have to expose your network to the internet. This reduces the attack surface and prevents external unauthorized access.
Unified Security Management
Admin By Request Secure Remote Access integrates with our PAM product to provide a single platform for managing both privileged access and remote sessions. This simplifies security management by centralizing control and ensuring consistency across all access points.
Approval Workflows
Our solution has approval workflows so organizations can control and monitor who can access critical systems. Users can request access which can then be reviewed and approved by designated administrators. So only authorized people can access sensitive resources and reduce the risk of unauthorized access.
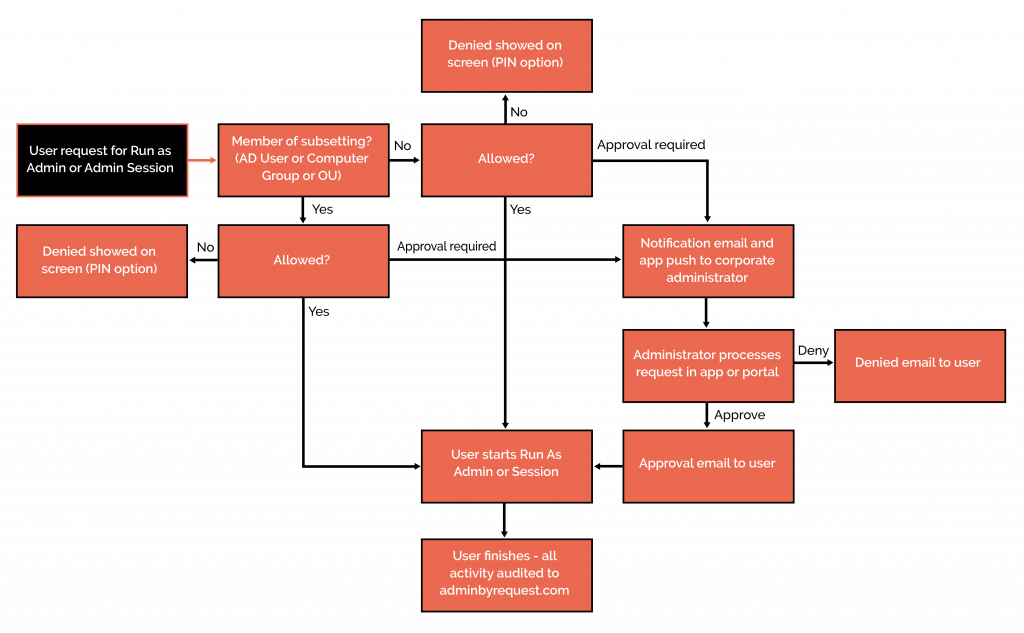
Detailed Auditlog
Every action taken through Admin By Request Secure Remote Access is logged in a detailed Auditlog. This feature provides a complete record of all activities, who accessed what, when and where as well as video recordings of remote sessions. This is essential for auditing, compliance and forensic investigations and provides visibility into user activity and system changes.
Inventory and Reporting
The integrated Inventory feature tracks all assets and access points in the network. This gives a real time view of the IT environment so you can manage resources and identify potential security holes. Combined with reporting capabilities you can generate reports on access activities, user behavior and system health to support proactive security and compliance audits.
Real-Time Alerting
Admin By Request Secure Remote Access has real time alerting which notifies administrators of any unusual or suspicious activity. Whether it’s an unexpected login or an unauthorized access request real time alerts allow for rapid response and minimize damage from security incidents.
Additional Security through Privileged Access Management
Being built on our PAM product, Admin By Request Secure Remote Access benefits from advanced security features like Just-In-Time access, least privilege enforcement and robust identity verification. So elevated privileges are only granted when needed and for the shortest time possible, reducing the attack surface.
User Experience
Despite all the security features, Admin By Request Secure Remote Access has a user-friendly interface. So technical and non-technical users can use the system efficiently and reduce the learning curve and encourage good security practices.
Scalable and Flexible
The solution is designed to be scalable and flexible for organizations of all sizes. Whether you need to secure access for a few users or thousands Admin By Request Secure Remote Access can scale. And it’s flexible in deployment, on-premises or cloud.
By using the features of our PAM product Admin By Request Secure Remote Access provides a complete, secure and user-friendly solution for remote access. All remote activity is secure, monitored and controlled so organizations can have peace of mind when protecting their sensitive data and systems and reduce the risks associated with traditional Remote Desktop.
Conclusion
Remote Desktop is a valuable tool for accessing and managing remote systems, but it is crucial to consider the security implications and follow best practices. For organizations seeking a more secure alternative, Admin By Request Secure Remote Access offers comprehensive features that ensure safe and efficient remote access. Try Admin By Request free today and enhance your organization’s remote access security.











